/etc/services
/etc/services maps service names into port numbers, and
typically needs entries for safetp and raw-ftp. The
safetp port is where sftpd will listen for incoming
connections, and the raw-ftp port is where sftpd will
contact ftpd, the normal (unencrypted) Unix ftp daemon.
# example entries in /etc/services
ftp 21/tcp safetp
raw-ftp 351/tcp
Typically, sftpd should be installed on port 21 (the usual
FTP port), and ftpd should listen to another port in the
protected range (<1024), such as 351.
If it is undesirable to have sftpd listen to 21, port 353
is the suggested alternative.
/etc/inetd.conf
/etc/inetd.conf maps service names to daemon executables.
inetd reads this file when it starts-up, and whenever it
receives the HUP signal.
# example /etc/inetd.conf excerpt
# svc type prot wait? user executable command-line w/argv[0]
safetp stream tcp nowait safetp /home/safetp/sftpd sftpd -f351 -s -y/home/safetp
raw-ftp stream tcp nowait root /usr/sbin/tcpd wu.ftpd -t0
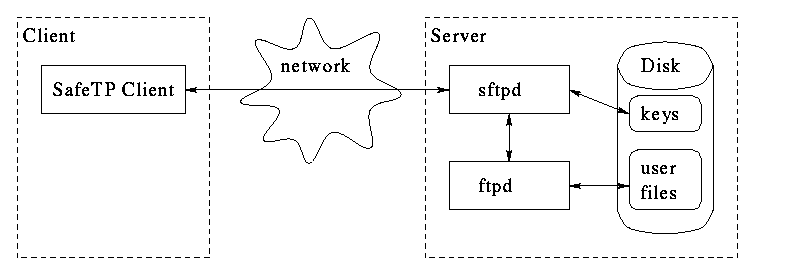
Who runs as root
sftpd does not have to run as root. For enhanced
protection against possible bugs in sftpd, it is preferable to
run as an ordinary user, with privileges only to read and write the
directory containing the cryptographic keys.
ftpd, because it must potentially access any user's home directory,
must run as root.
inetd, because it must listen to protected (<1024) ports, and
spawn servers running as arbitrary users, must run as root.
kftpd (Kerberos' ftpd), if you're using
Kerberos compatibility, must run as root for the same reason that
ftpd does, plus it must access sensitive Kerberos keys.
Encryption
Encryption is used to provide two security services: authentication and
confidentiality.
Server authentication is provided via DSA (Digital Signature Algorithm)
public-key signatures. The server has a public and a private DSA key.
Clients usually receive the server's public key during the first contact,
trusting that the first contact is authentic, and record this public key
in a local database. Subsequent connections are authenticated when the
server proves it knows the corresponding private key.
Confidentiality is bootstrapped via ElGamal public-key encryption. Clients
generate ElGamal keys locally, and transmit their public keys when they
connect to a server. The server encrypts the master session key with the
client's public key; the client is then the only party that can decrypt it.
Message-level authentication is provided by an HMAC (Hashed Message
Authentication Code) using SHA (Secure Hash Algorithm) as the hash
function, for which the keys are derived from the master session
key.
Message-level confidentiality (including confidentiality of the user's
password) is provided by Triple-DES (Data Encryption Standard), for which
the keys are derived from the master session key.
Key Management
The DSA private key, and the random seed file, are stored on disk
in plaintext (unencrypted).
Compromise (unauthorized read or write) of either file can lead to a
compromise of user's passwords. It is therefore essential that file
permissions be set properly, and that these files not be transmitted
via an insecure network protocol such as NFS (Network File System).
Various additional key protection measures have been considered, such as
encrypting with a fixed (compile-time) Triple-DES key, passwords entered
at boot time, etc. However, these measures are either insufficient or
too inconvenient for users, and therefore have not been employed.